ONSITE • REMOTE • CLOUD
Threat Detection
Either in its Managed Threat Hunting form or single-shot Compromise Assessment, TH offers a proactive approach to detect Threats. It leverages expert knowledge of attacker techniques and behaviors through by our DFIR and CTI experts to generate hypotheses and proactive searches. The final objective is to find signs of malicious activity in the client’s infrastructure, with special focus on threats that cannot be detected by other means.
| Managed Threat Hunting | Compromise Assessment |
|---|---|
| Our Managed Threat Hunting service offers intelligence-driven, proactive threat detection using a combination of DFIR methodologies and customized strategies. We work closely with clients to identify and mitigate potential security risks by executing recurring hunts on their networks, endpoints, and other security platforms. | One eSecurity’s Compromise Assessment (CA) service is a proactive cybersecurity solution designed to detect threats and security incidents within your systems. This one-time assessment helps identify potential breaches, focusing on threats that may evade traditional detection methods. |
| Learn more | Learn more |
What Is Threat Detection & Hunting?
How do you know your systems are not compromised?
One eSecurity’s Threat Hunting Service offers our clients a continuous and proactive threat search process in both their networks and systems. Our Hunting Framework combines manual and automated analysis carried out by our expert analysts in different areas. This approach transforms traditional threat management, turning it into a proactive operation and offering a much faster detection and response rate.
Our analyses are carried out through a comprehensive analysis of the environment, using both analytical and forensic techniques, targeting either global threats of specific profiled ones defined with the Client.
Why Threat Hunting?
Prevention systems alone are insufficient to counter focused human adversaries who know how to get around most security and monitoring tools. - From SANS Institute.
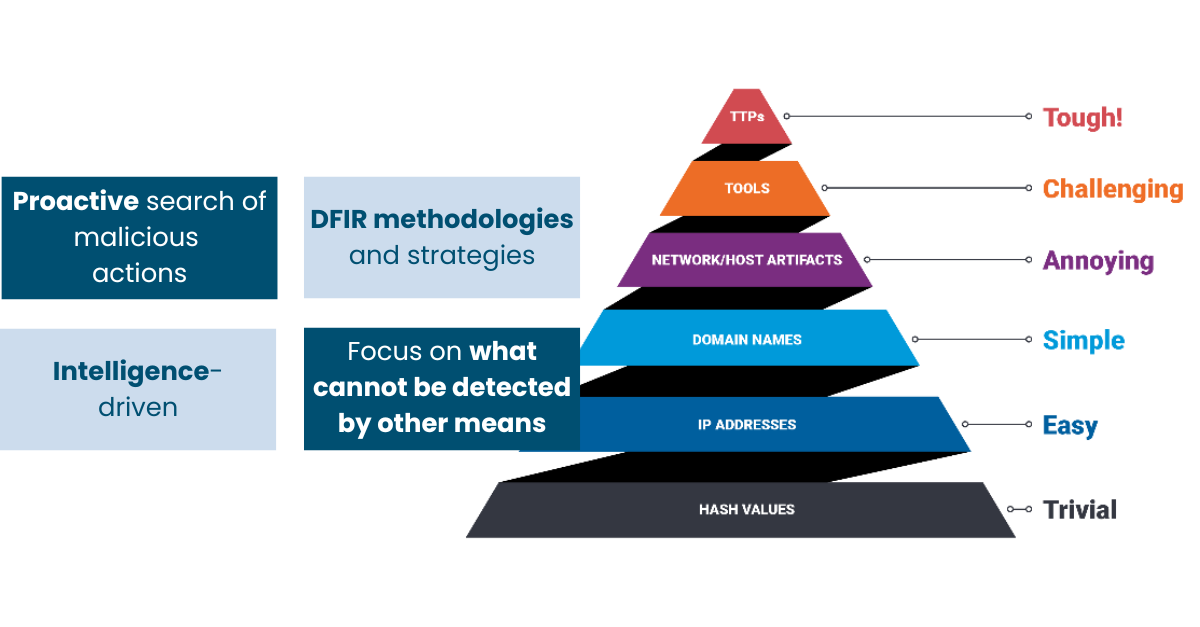
- Wide variety of TTP and Threats continuously covered
- Focus on what cannot be detected by other means
- Intelligence-drive
- Not high dependency on technology
- Lower number of alerts and False Positive
- Able to detect unknown threats
Hunting Framework
Our years of experience have allowed us to develop our very own Hunting Framework on which we build our service.
Thanks to this framework we are able to:
- Improve and automate the prevention of security incidents through control measures.
- Feed information to other perimeter security devices.
- Focus on specific campaigns or conduct beats to identify APTs.
- Automate security operations and remediation activities.
- Improve incident detection.
- Provide information to different company areas of operation.
Our reliable external sources of threat intelligence obtained from different feeds (OSINT, HUMINT, CCI, IOCs, Malware analysis) combine with your company's own internal sources to form the perfect cocktail of information necessary to counteract and prevent possible attacks.
This framework combines specialist resources, technology, and dedicated processes.
Resources
The Threat Hunting service collates the capacities and expertise of our Incident Response, Cyber Threat Intelligence, and Threat Hunting departments. Experts in each of these areas will be responsible for generating the various IOCs (Indicators of Compromise) and TTPs (Techniques, Tactics, and Procedures) which will be used to identify threats. Moreover, these experts are in charge of supplementing the automated threat analysis by doing their own manual analysis, ensuring that any threats within the client’s systems and networks are detected, and also carrying out malware analysis if needed.
Technology
The Threat Hunting platform is part of our Incident Response framework, which we have named Forest. This platform has over 10 years of experience and has been used by us and our clients on dozens of investigations around the world. The analysis of thousands of devices in a few hours and the versatility of this platform have been key in the resolution of all types of cases: financial actors, ransomware, or insiders, among others.
Dedicated Processes
All processes defined by the Threat Hunting service are designed to be integrated with existing processes, some of which are well developed, and exist within the incident detection, prevention, and response cycle, adding value at each phase through existing CERT, SOC or CTI teams.
What Do We Hunt?
Hunting Threat Actors and much more…
- Threat Actors: We hunt the most relevant cyber-criminal groups
- Generic TTP: The most commonly used by TAs, using sources such as Red Canary
- Bad Practices: We detect them to avoid potential incidents
- Malware: Malware most used by TAs such as Mispadu or Grandoreiro
- CVE: Based on our customers software
- Anomalies / Outliers: Look for deviations in the data based on AI, correlation, etc.
And not only with EDRs
- UNIX
- Routers
- SIEM / Other data sources
How We Do It? - Advanced Threat Detection
A Traditional SOC is Not Good Enough
Different approaches (initiatives) for advanced detection
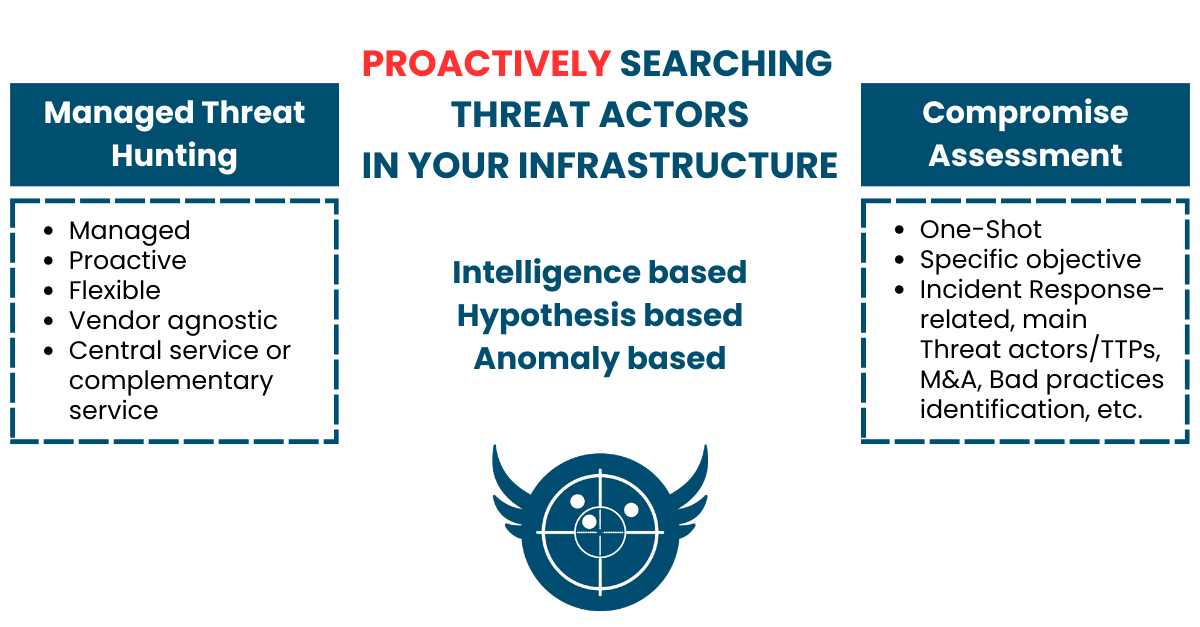
Managed Threat Hunting
- Managed
- Proactive
- Flexible
- Vendor agnostic
- Central service or complementary service
Compromise Assessment
- One-Shot
- Specific objective
- Incident Response-related, main Threat actors/TTPs, M&A, Bad practices identification, etc.
Software and Hardware
- Periodic non-continuous expert analysis in platforms alerts
- Flexible
- Organizations without a SOC
Level 3 Analysis (expert escalations)
- Expert analysis or complex alerts
- DFIR and Threat Hunting approach
- Organizations without Internal expertise or resources to analyze reported alerts
SOC Detection Improvements
- SOC Assessment (gap and improvements)
- Data Source Analysis and detection improvements
- SOC Use Cases integration
What Advantages Do We Offer Compared To Our competitors?
Our Threat Hunting service formula is:
Threat Hunting = Response to Incident - Incident
A Different Approach
Our approach is different and more efficient than reactive systems. Drastically reduces the volume and severity of attacks leading to an order-of-magnitude fewer alerts, incidents, and costs. Provides early warning and indicators to model zero-day signatures to incident response mechanisms and enumerate attack networks through cyber threat intelligence. It is not subject to scalability issues around performance and cost that reactive systems struggle with. One eSecurity threat hunting decisively engages the adversary and also includes activities to hunt and pursue adversaries.
Our Own Framework
Having our own hunting and threat intelligence framework enables us to: analyze and generate all kinds of IOCs, from the simplest hash files to the most elaborate TTPs, based on our malware analysis ability; perform these analysis on large banks of servers and equipment, quickly detecting the type of attack, the artifacts found and patterns on files, processes, ports, registry entries, installations, memory logs, and disks; integrate the framework with the client's own tools (antivirus programs, EDRs, forensics agents, etc.); reuse all the information generated to achieve rapid detection and containment of any type of malware.
Flexibility
You can activate us whenever you need to and for whatever purpose. Our different service agreements allow the client to have Threat Hunting as a one-shot services or as a continuous Hunting service, 24/7, with thousands of targets.
Related To Our Services
| Digital Forensics and IR | Emergency Incident Response | Cyber Threat Intelligence |
|---|---|---|
| One eSecurity Digital Forensics service is focused on system in-depth analysis, aiming at obtaining a traceable record of previous activity in order to answer any investigative questions. | One eSecurity Emergency Incident Response is aimed at clients who need agile response and support when a security incident happens. | The Cyber Threat Intelligence service by One eSecurity provides (both internally and for clients) knowledge and information on key threats for decision-making and forecasts of risk situations on IT systems and networks. |
| Learn more | Learn more | Learn more |