ONSITE • REMOTE • CLOUD
CyberExercises
Engaging your teams in realistic simulations, we test and prepare human and managerial factors for cybercrisis. We challenge incident response plans and playbooks and address response and resilience improvements. This service applies all the experience gathered by One eSecurity over the years from our Emergency Incident Response, Digital Forensics, and Threat Hunting Units and provides the best approach and fit for each client.
Looking for a way to sharpen your cyber readiness skills? Our Workshops offer knowledge-packed sessions based on real cyber incidents - Learn from real attacks, dissect key mistakes and successes and enhance your preparedness:
| Workshops |
|---|
| A hands-on workshop based on anonymized real-world incidents. Our workshops are sessions designed to put participants in real-life scenarios through structured response activities. They are adaptable to different organizational roles (C-Level, Management, Technical) |
| Learn more |
What Is CYBEX?
Test and prepare cyber crisis human and managerial factors through realistic adapted cases
One eSecurity's CYBEX Service offers simulations of real cybersecurity incidents that your team will probably have to face sometime soon.
There are many different types of Cyber Exercises, ranging from a single challenge for your technical team in a hypothetical scenario, to a real and complete tabletop involving the crisis management team, making decisions based on real information coming from other areas or groups.
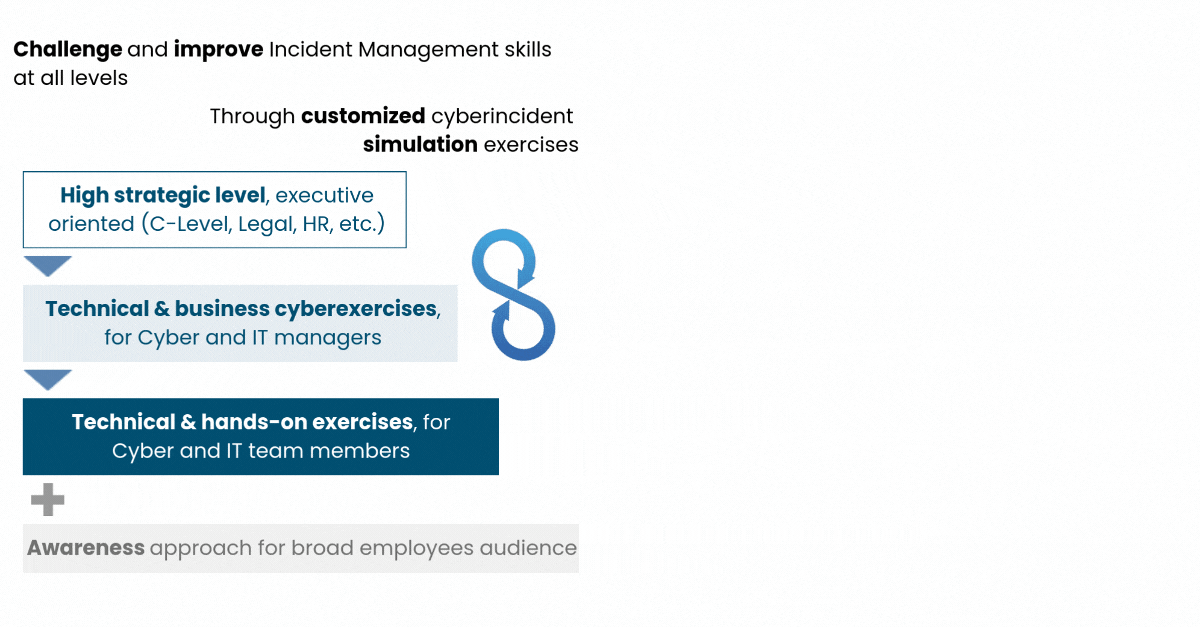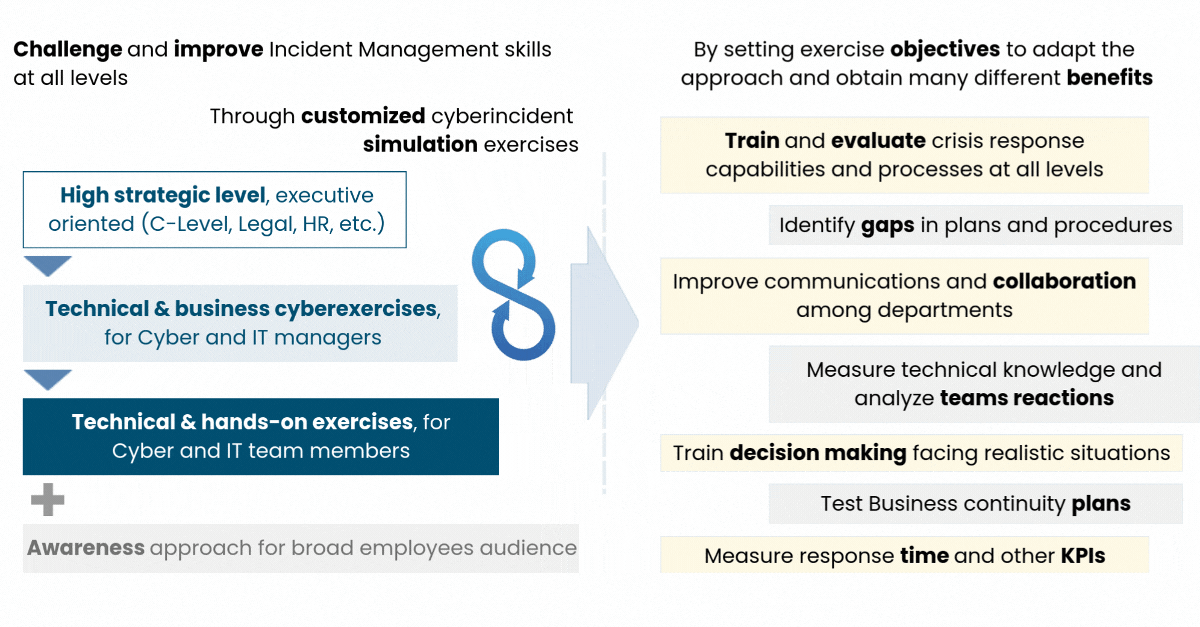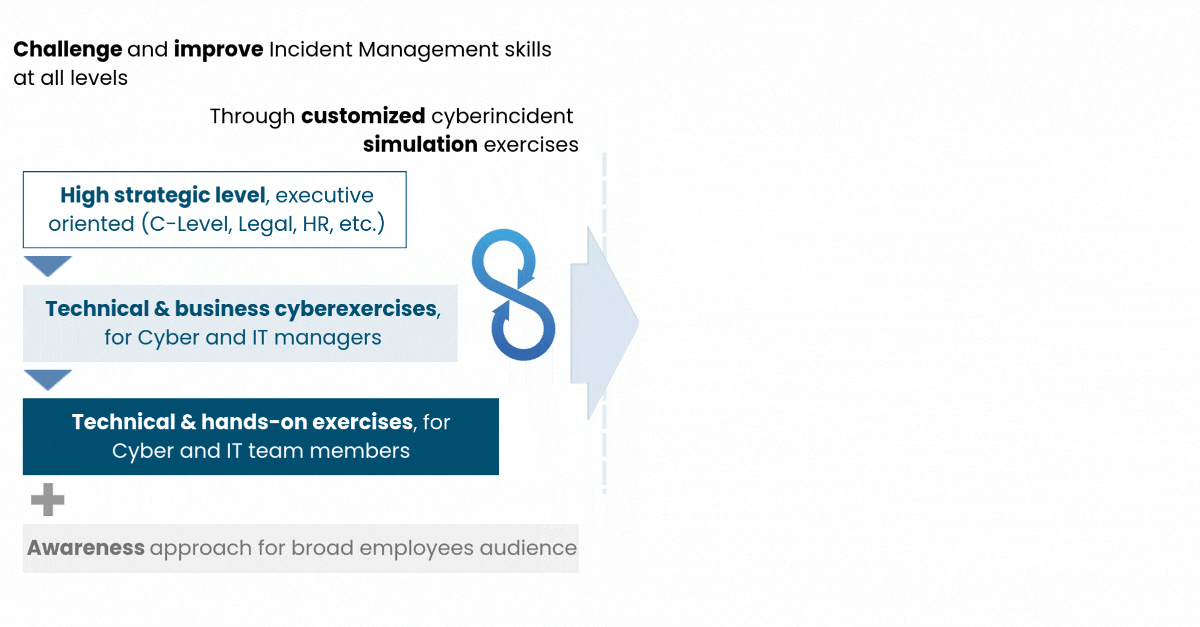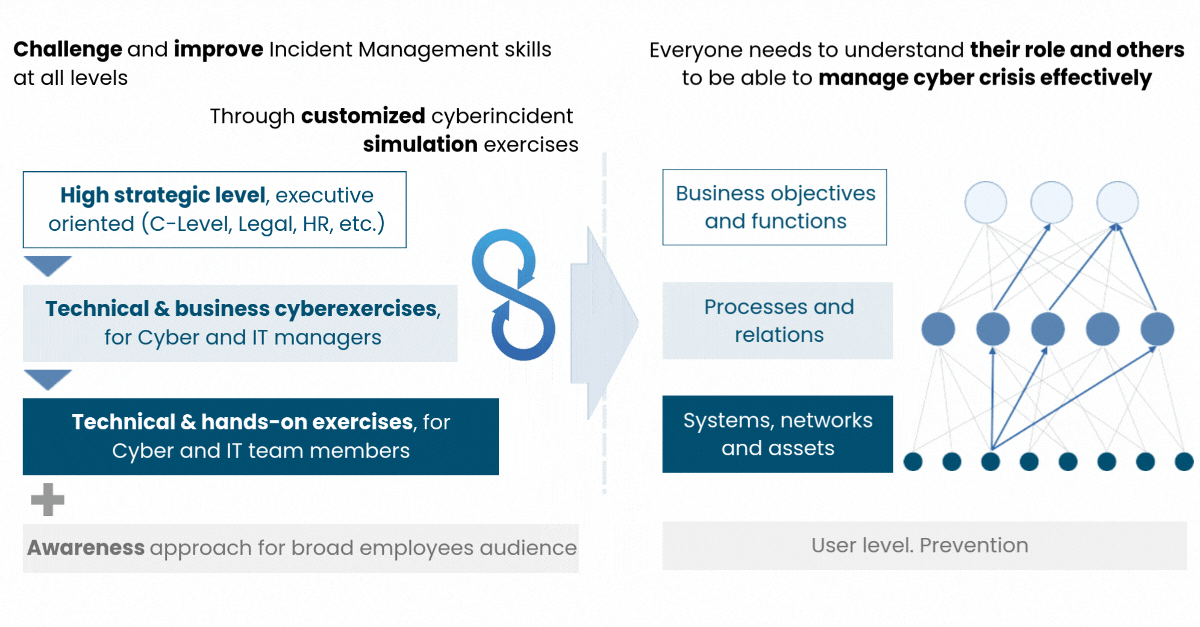
A Cyber Exercise can have different approaches and perspectives according to the client’s goals and objectives. These goals can be focused on evaluating the response capabilities and the internal knowledge of the company's processes, identifying gaps in plans and procedures, measuring the technical knowledge of the team, and analyzing how the teams react, measuring response time, testing business continuity plans, etc. They can also serve as a training for different departments/areas/committees, evaluating their relationship models and interfaces, and analyzing how they work together.
Why Should You Use CYBEX?
The One eSecurity's Cyber Exercises approach is based on real cyber threat situations adapted to the operational environments of our clients.
Scenarios can be precisely adapted to the client’s needs or demands. They can also aim to resolve existing weaknesses in the organization or consolidate strengths, to increase the level of effectiveness with which threats are contained or neutralized, or to improve the detection and reduce the potential damage of incidents, when they arise.
The alignment of objectives, perspectives (strategic, tactical, and operational/technical), and teams involved, set the strategy that marks a successful exercise. Besides the topics mentioned above, there are also other factors that affect the design and scope of the Cyber Exercises. These factors are:
- Communications and interaction with stakeholders/regulators/other CERTs.
- Hypothetical scenario versus real threat.
- Simulated outputs logs/artifacts/clues as input or injects to the cyber exercise.
- Simulated versus emulated.
- Tactics, Techniques, and Procedures used by the adversary and type of threats.
- Use of real roles versus generic groups.
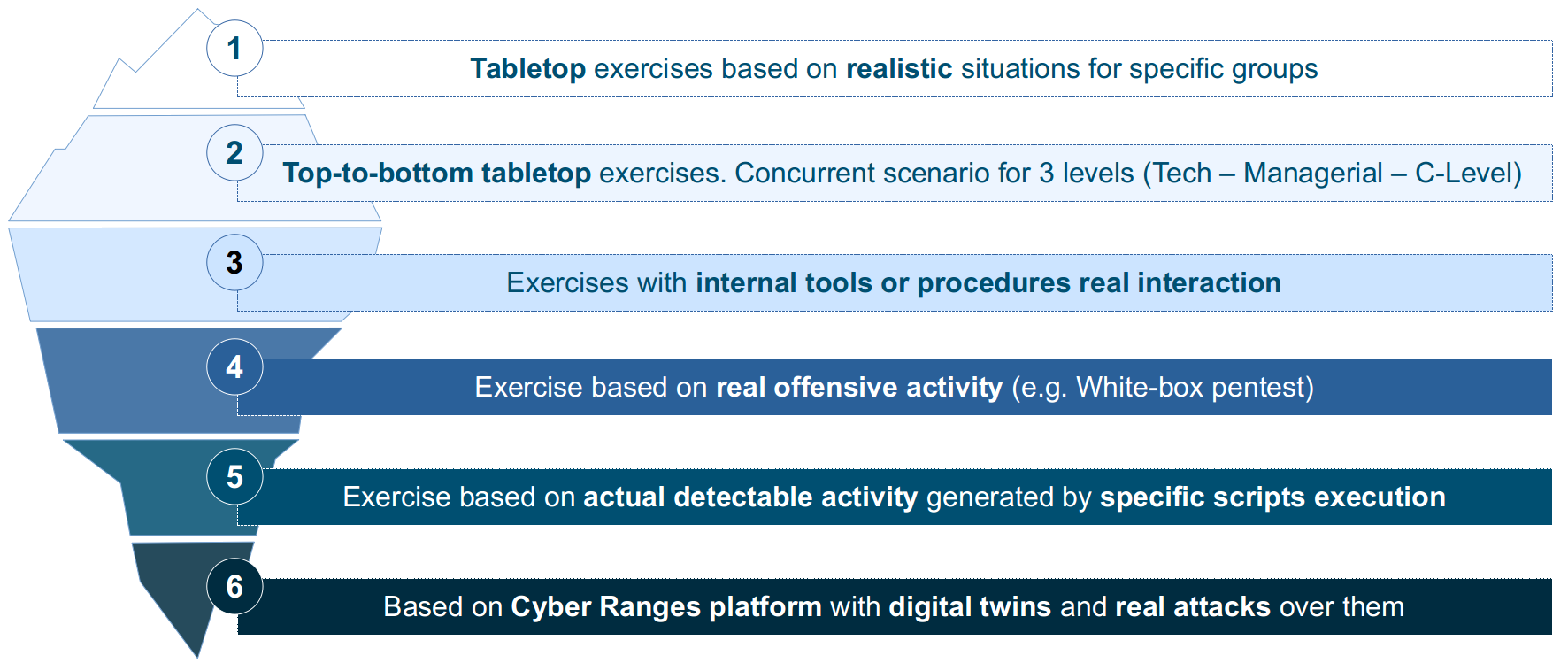
Types of CYBEX
These can be executed in different ways depending on the immersion level and objectives
One eSecurity understands the aforementioned factors, options, and criteria, and it has established the following types of cyberexercises in order to cover all possibilities:
Exercises are based on realistic scenarios completely tailored with relevant techniques, risks, context and needs
Different realistic topics can be designed:
Ransomware
Attack by a known group encrypting information and spearphishing email vector
Insider
Company employee who, after a discontent, exfiltrates information for non-permitted uses
Supply-chain - Third party
Supplier/third party is compromised privileges are used to enter the company and commit the attack
Extortion
Advanced version of ransomware also involving data exfiltration or DoS blackmail from a criminal group
Covert attack
Ransomware that diverts attention while adversaries are targeting critical infrastructure or doc exfiltration
IT attack with movement to OT
Compromise starting at administrative network that escalates to industrial equipment and production
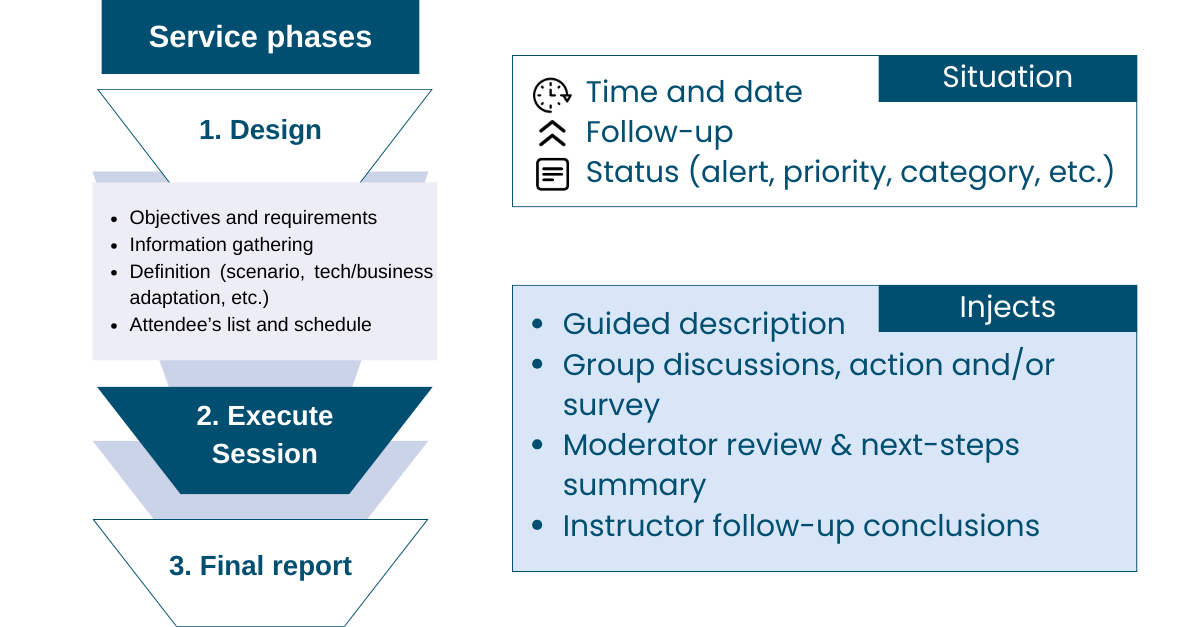
Methodology
One eSecurity uses its own methodology that combines its experience and processes to build the most appropriate attack scenario. This methodology is based on best practices and includes three phases, starting with the definition phase in which One eSecurity identifies the client's needs and requirements, acquiring knowledge of their operational environment in order to imitate this in the cyber exercise.
Session execution at a high level
Design Phase
In the Design stage we develop a workshop with key client staff members to understand the real threats, threat agents, vulnerabilities, and critical assets. Combining these, we will propose two or more scenarios for the client to select.
One eSecurity designs the cyber exercise chosen by the client:
- The definition of different synchronous and asynchronous injects, also called events, with timeline.
- The description of the crisis management plan and/or IR Plan, with the expected actions.
- The alignment of both the injects and the actions of the defined plan.
In the next steps, One eSecurity considers existing workflows/IRPs or playbooks in order to refine the Cyber Exercise (continuous improvement) and include company platforms/committees to complete the scenario’s context. One eSecurity develops and reviews all the required material for the day (videos, speeches, notes, screens, and review physical accommodation etc.).
Execute Session
According to the committees and roles defined in the crisis management plan and/or IR plan, One eSecurity organizes teams in round-table environments during the exercise and gives them a predefined time for each and every inject to collaborate, and agree on actions and decisions between the different defined teams.
Once the inject time is over, the One eSecurity exercise leader discusses with the participants the actions and decisions that were taken and gives recommendations according to best practice. During the exercise, One eSecurity staff will document the decisions and actions of the teams, in order to write a final report on the effectiveness of the company’s response.
Final report
A final report that contains the analysis, lessons learned, recommendations, and conclusions of the exercise will be delivered to the client according to each of the phases of the incident response:
- Detection
- Initial response
- Containment
- Eradication
- Recovery
- Lessons learned
After the execution, we deliver a final report including analysis details and conclusions arising from the objectives defined at the Design Phase
Related To Our Services
| Cyber Consulting | SANS Training | Cyber Threat Intelligence |
|---|---|---|
| One eSecurity CYCON service can give you honest answers to the most complex questions and acting as a guide throughout decision-making processes. | One eSecurity is partner of the SANS Institute in Spain, the worldwide leader in cybersecurity training. | The Cyber Threat Intelligence service by One eSecurity provides (both internally and for clients) knowledge and information on key threats for decision-making and forecasts of risk situations on IT systems and networks. |
| Learn more | Learn more | Learn more |