ONSITE • REMOTE • CLOUD
CyberInsurance
Focused on measuring the damage and assessing the best response for both the insured and the insurer by effectively Responding to cyberincidents through Cyber Insurance policies and coordinating with all Client, Insurance company, Broker, third parties, etc. We have experts that help both Clients and Insurer to effectively deal with the situation at technical, managerial and coverage levels improving the loss ratio.
What Is CYBINS?
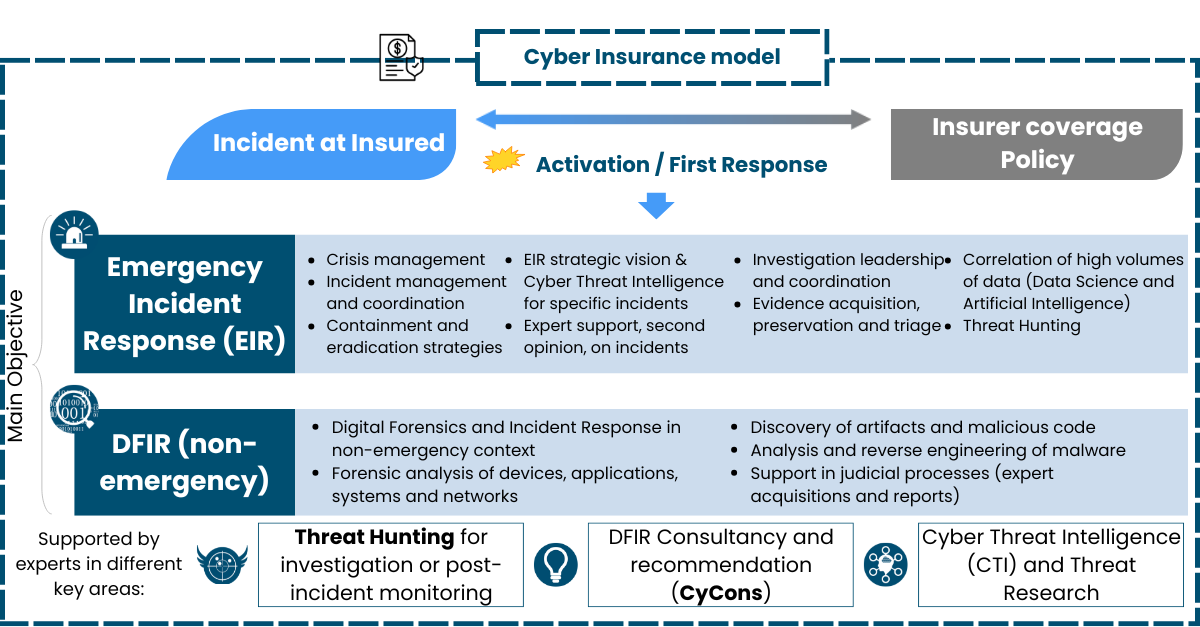
One eSecurity's CYBINS Service helps insurance companies panel Emergency Incident Response services which are subject to their clients' cyber policies.
Cyber attacks pay no attention to working hours or borders. Insurance companies provide services for large corporations, so they need to have experts available 24x7x365, anywhere in the world. Moreover, these experts must have tools that can be adapted to any technological solution used by users and be prepared to deal with all actors within the value chain.
When dealing with cybercrime, companies must activate contingency plans, and insurance companies must support them throughout the incident. In this scenario, cybersecurity experts with extensive knowledge and experience in Forensic Emergency Incident Response are required. Their role is to evaluate the extent of the damage and assess the best response, both for the policyholder and the insurance company. The aim is to protect companies and prepare insurance companies.
Specifically, detection and investigation are two primary cost centers in the work to protect against Insider Threats. Companies are significantly increasing their spend in those two activities, with investigation costs increasing by 86% in only 3 years. (Ponemon Institute 2020)
Why CYBINS?
A cyber incident can have devastating consequences for the attacked party. Contemporary cyber threat management is not limited to IT, but is defined by coordinating the three defense lines and Board-led governance. Integrating the response to technological threats is only possible with the active collaboration of experts in each of the organization’s operational areas. This also requires knowledge of the business, the assets that support continuity, and the financial assessment of the maximum possible losses. In short, their preparedness in the event of a crisis must have an appropriate resilience level.
While some companies may have cybersecurity knowledge in the context of incident response, a few may have over 10 years of experience in incidents in the context of big international organizations, and a very small number may have experience in the cyber insurance sector; One eSecurity offers expertise across all three fields.
One eSecurity helps policyholders to reach the organizational resilience indicators required to have an appropriate cyber threat management. This is achieved by providing a response in the most critical moment and developing together the necessary maturity levels to meet these goals.
Chronology
Helping our Clients through their Cyber Insurance policy
The following diagram shows the Cyber Insurance flowchart from incident detection (1) to insurance Compensation (5), showing insurance coverage by Insuerer and technical response and coordination by One eSecurity.
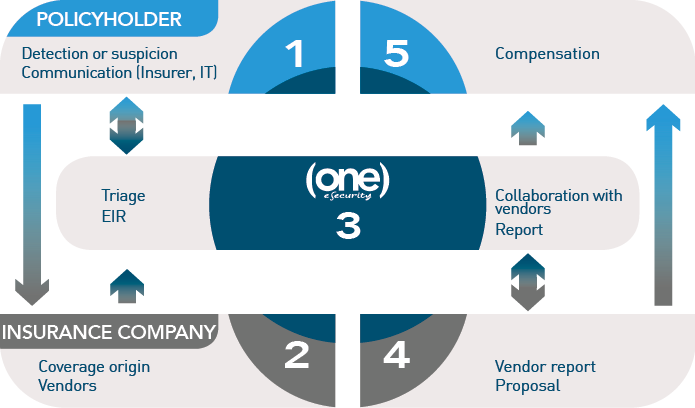
Once the mode of operation has been agreed, One eSecurity immediately provides the insurance company with the human and technical resources that may be needed for any type of incident, based on these stages:
Detection
The policyholder detects, or even merely suspects, a security breach. This causes the insurance policy to be activated.
Triage
An initial triage is done by carrying out a series of consultations with the policyholder in order to determine the authenticity, type, and scope of the incident.
Foresight
One eSecurity assesses the project needs: technical resources, equipment, travel, purchases, methodologies… in order to provide an initial estimation and book the hours for the insurance company, when possible.
Response
If the incident is “live” One eSecurity activates the response mechanisms to mitigate it.
Coverage check
As One eSecurity verifies the origin of the incident, it confirms the circumstances with the insurance company in order to check the coverage.
Investigation
If the event is covered, then the investigation continues, under the limited conditions set in the insurance policy (deductibles).
Collaboration
When the incident requires the participation of other parties included in the conditions (lawyers, claims adjusters, crisis manager…), One eSecurity will offer full collaboration to achieve optimal incident management.
Report
During the investigation process, interim reports on the evolution of the case will be drafted, covering the scope of the case, the detected implications, the assets affected, the lateral movement of the attacker, the consequences, etc, based on digital evidence. At the end of the investigation, the final technical report will be issued, similar to the interim drafts, including all the findings, the chronology, any technical explanations, causes, identified actors, etc, as well as the conclusions that make it possible to link the incident to the type of insured scenarios.
Expert report
As an option, One eSecurity can also write a more exhaustive expert report that can be used in those cases that end up in court, and hence having judicial application.
What is behind CYBINS?
One eSecurity’s CYBINS service is based on its core business, the Incident Response services (DFIR/EIR), which include, among other, incident management/response, malicious code discovery and analysis or forensic analysis, for the cybersecurity policyholders. Moreover, One eSecurity offers insurance companies a wide range of DFIR projects and services in order to satisfy the needs and demands of their policyholders.
Cyber Insurance Risk transfer model to deal with a Cyberincident when it happens
Service agreements
In order to deliver the services, One eSecurity suggests using the Retainer service agreement which offers a bank of hours appropriate to the needs of the insurance company, which can incorporate different team profiles. These services are delivered as required, and to the response times requested, including Principal, Senior and Junior profiles.
The advantages of the Retainer service agreement lie in the fact that the insurance company can be certain that the resources provided by One eSecurity will be available 24x7x365 anywhere in the world the policyholder may need. This while following the strictest service requirements that allow achieving the goal that the insurance company has agreed in the wording with the policyholder.
At the beginning of the incident One eSecurity will estimate the number of hours needed for the specific case, and at the end a report (Hour Consumption Report) will be produced including a specific breakdown of the hours devoted to the incident and the remaining hours that are yet to be used. Also, One eSecurity will issue a document justifying the costs associated with the incident and the specific hours worked.
The insurance company can extend this bank of hours when 80% of the total time has been used. At this point, the company will be asked whether they would like an extension.
As an alternative way of working, we offer On demand . With this service mode the insurance company will be able to access the services previously mentioned based on the technical and human resources that One eSecurity has available at that specific time, but without the complete assurance of the SLAs included in the Retainer service agreement.
What Advantages Do We Offer Compared To Our Competitors?
One eSecurity offers efficiency in its service to all participants involved:
- Insurance company: reduction of loss ratio through the automation of forensic investigation processes thanks to the SKY system developed by One eSecurity. This system reduces the time spent investigating incidents with a high number of devices to analyze, which in turns reduces the response service cost.
- Policyholder: incident resolution, fulfilling the commitments of the insurance policy
- Collaborators: comprehensive explanation of the investigated incidents to provide support and coordination in legal matters, crisis, notifications…
One eSecurity offers some benefits in its CybIns service:
- Collaboration with insured, insurer, broker and lawyers for a coordinated and efficient response.
- Immediate and coordinated response with technical areas (CISO) and Insurance (Risk and/or Insurance Manager)
- Mastering insurance language: wording, conditions, triggers, exclusions.
- Neutral vendor: own infrastructure compatible with any architecture
- Worldwide: on-site or remote
- Availability 24 x 7 x 365
Related To Our Services
| SKY | Cyber Threat Intelligence |
|---|---|
| SKY provides our clients with advanced digital remote investigation & forensic capabilities for their companies and their Computer Incident Response Teams (CIRTs). | The Cyber Threat Intelligence service by One eSecurity provides (both internally and for clients) knowledge and information on key threats for decision-making and forecasts of risk situations on IT systems and networks. |
| Learn more | Learn more |