ONSITE • REMOTE • CLOUD
What Is Compromise Assessment?
Uncover threats you didn't know were there
A Compromise Assessment is a structured cybersecurity evaluation designed to determine whether an organization's IT environment has been compromised. It involves an in-depth investigation using forensic techniques and threat intelligence to detect signs of past or ongoing cyber threats. By leveraging threat-hunting methodologies, it identifies malicious activity that may have bypassed traditional security measures, providing organizations with a clear view of their security posture.
This assessment helps organizations uncover security gaps, detect unauthorized access, and evaluate their exposure to cyber threats. By proactively assessing the environment, businesses can take informed actions to strengthen their defenses, mitigate risks, and prevent potential security incidents from escalating.
Why Should You Use Compromise Assessment?
One-Shot Threat Hunting for Specific objectives
Compromise Assessment is crucial for organizations looking to secure their infrastructure, detect hidden threats, and validate their security posture. It is particularly useful in the following scenarios:
Mergers and Acquisitions (M&A)
During M&A activities, organizations need to ensure that the target company is free of existing cyber threats before integration. A Compromise Assessment helps identify any hidden security risks that could be inherited.
Threat Actors and TTPs
If an organization in the same industry has been targeted by a cyberattack, there is a risk of similar attacks spreading. Additionally, after penetration tests, unexpected data exfiltration findings may necessitate an assessment to determine if a compromise has already occurred.
Current Security Posture Evaluation
Organizations conduct periodic Compromise Assessments to verify whether any undetected Advanced Persistent Threats (APTs) or other malicious actors are operating within their network.
Employee Malpractice and Insider Threats
Security breaches can occur due to negligence or intentional malicious actions by IT administrators, cybersecurity personnel, or other employees. A Compromise Assessment can identify unauthorized activity, policy violations, and security misconfigurations.
Incident Response Verification
After a cyber incident, organizations need to ensure that the threat has been fully eradicated. A Compromise Assessment verifies that no persistence mechanisms, backdoors, or residual threats remain within the environment, providing confidence in a clean recovery.
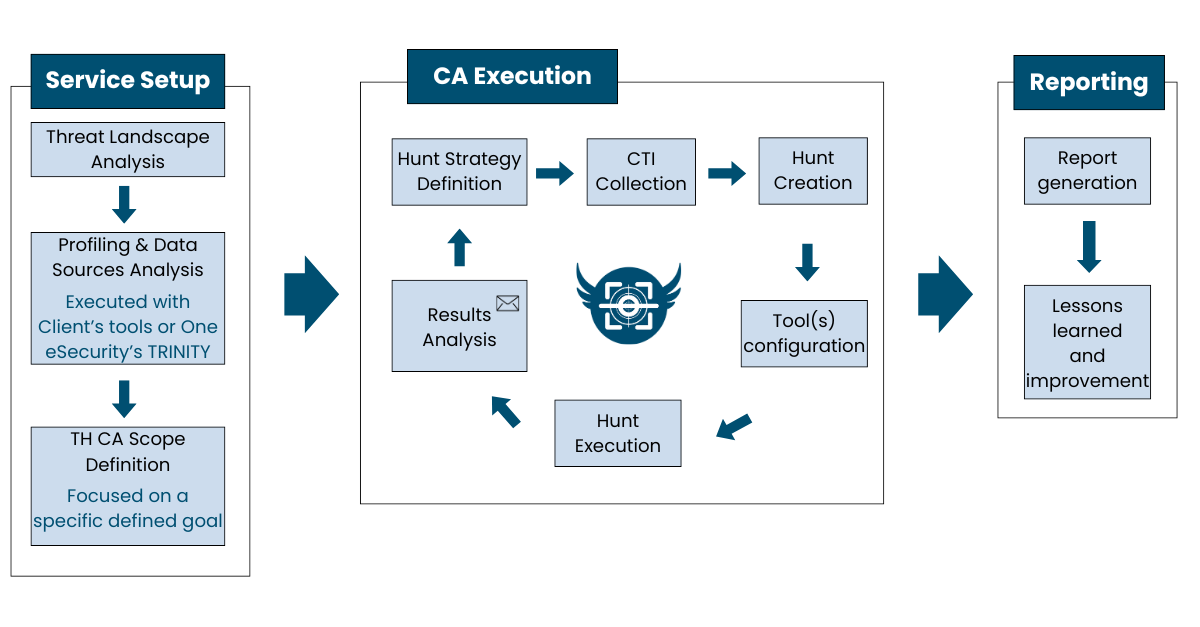
Methodology
High level continuous Threat Hunting process
As a targeted threat-hunting operation, the Compromise Assessment leverages both internal cyber intelligence from One eSecurity and external intelligence from a Threat Landscape Analysis specific to the organization. This approach allows for a more precise use of security tools, such as networks, EDR, XDR, and SIEM, to launch specific queries and detect malicious actors within the client’s systems.
The strategies used in the assessment include:
- Automated analysis of servers and endpoints: Detecting malicious activities by reviewing artifacts, file patterns, processes, ports, registry entries, logs, memory, and disks across various platforms.
- Integration with client security tools: Incorporating antivirus software, EDR solutions, and other security agents into our Hunting Framework, enabling rapid threat detection and comprehensive attack scope evaluation.
- Customizable execution strategy: The assessment can be performed within an agreed timeframe and frequency, allowing for both one-time evaluations and recurring assessments tailored to the organization's needs.
Throughout the process, any detected findings or alerts are immediately communicated to the client. At the end of the assessment, a detailed report is provided, outlining findings, TTPs, tools used, and anomalies detected. This intelligence-driven report focuses on identifying threats that traditional security measures may have missed, ensuring a thorough and actionable evaluation.
Contact Us
If you would like to learn more about One eSecurity's Compromise Assessment service and how it can help your organization assess and mitigate threats, please do not hesitate to contact our team.
📩 Request more information at sales@one-esecurity.com
⚠️ Experiencing a cyberattack? REPORT AN INCIDENT
Related To Our Services
| Digital Forensics and IR | Emergency Incident Response | Cyber Threat Intelligence |
|---|---|---|
| One eSecurity Digital Forensics service is focused on system in-depth analysis, aiming at obtaining a traceable record of previous activity in order to answer any investigative questions. | One eSecurity Emergency Incident Response is aimed at clients who need agile response and support when a security incident happens. | The Cyber Threat Intelligence service by One eSecurity provides (both internally and for clients) knowledge and information on key threats for decision-making and forecasts of risk situations on IT systems and networks. |
| Learn more | Learn more | Learn more |