ONSITE • REMOTE • CLOUD
What Is Managed Threat Hunting?
Cyber threats are constantly evolving, and traditional security measures alone are no longer enough.
Threat Hunting: A Proactive Search for Threats
Managed Threat Hunting is a proactive cybersecurity approach designed to actively search for hidden threats within an organization’s environment. Unlike standard security monitoring, which relies on alerts and predefined attack patterns, Managed Threat Hunting leverages advanced detection techniques, adversary behavior analysis, and cyber threat intelligence to uncover sophisticated threats that evade standard defenses.
'The goal of threat hunting is not only to find more security incidents but to improve automated detection capabilities over time.' David Bianco, SANS Institute Instructor.
'To catch intrusions in progress, rather than after attackers have completed their objectives and done worse damage to the organization.' SANS Institute.
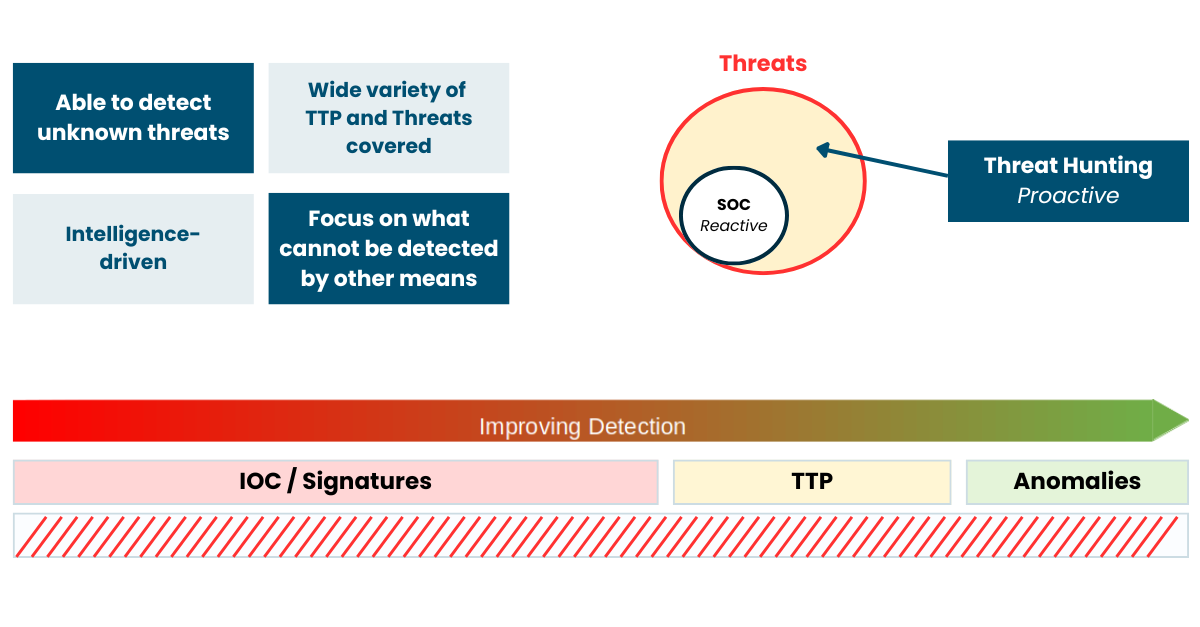
Why Should You Use Managed Threat Hunting?
In today’s cybersecurity landscape, organizations need a balanced combination of reactive and proactive detection. While Security Operations Centers (SOC) provide continuous monitoring and respond to alerts, Threat Hunting complements this approach by proactively identifying threats that may have bypassed traditional detection mechanisms. Integrating both approaches enhances your organization’s ability to prevent and respond to cyber threats effectively.
Reactive Detection
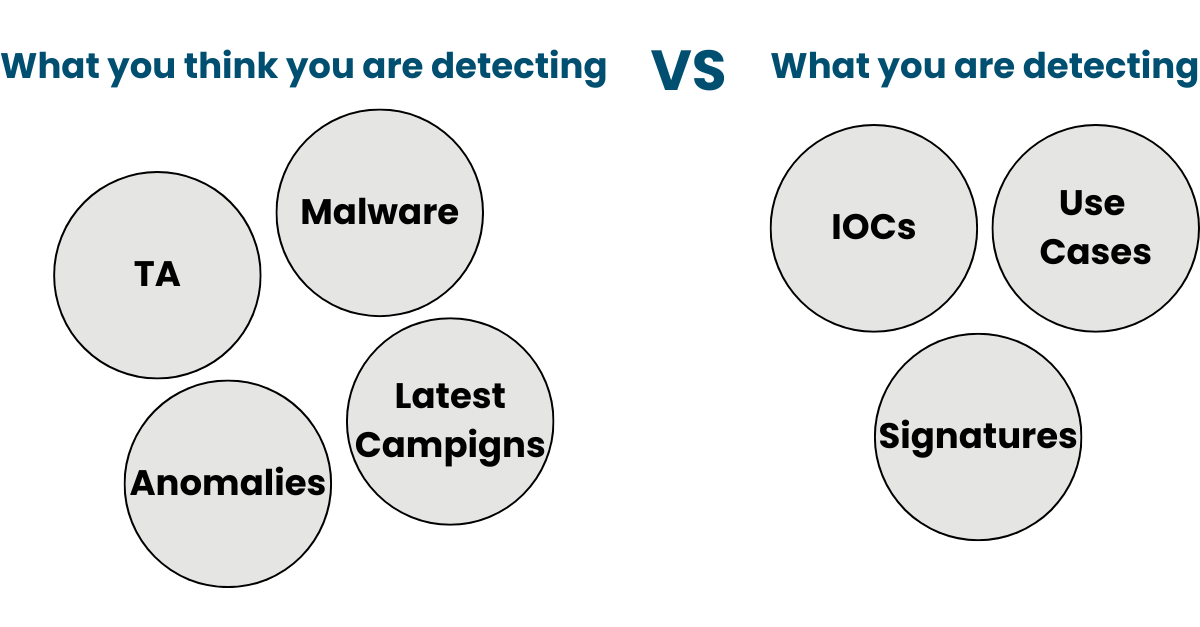
Proactive Detection: Threat Hunting
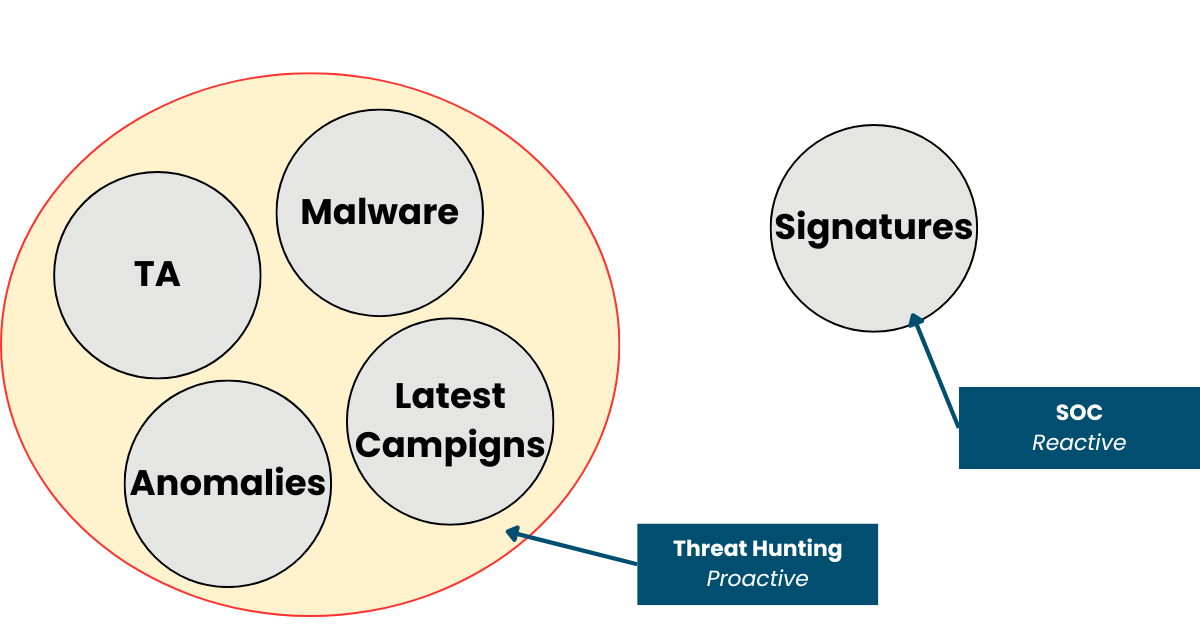
Threat Hunting gives you the protection you think you already have (but you don't)
'Ransomware, the main threat nowadays, is the Top 2 threat that hunters detect in a daily basis' SANS Institute.
'Resources spent on remediation are reduced 39% in organizations doing Threat Hunting' SANS Institute.
Organizations can no longer afford to operate without Threat Hunting:
- Detecting Stealthy Threats: Threat Hunting is the only way to identify advanced persistent threats (APTs) and stealthy attacks that evade automated security tools.
- Uncovering Security Breaches: It helps detect security breaches that remain undetected for extended periods, minimizing potential damage.
- Tracking Threat Actors: Identifies and analyzes adversary tactics, techniques, and procedures (TTPs) to understand and mitigate their impact.
- Leveraging Cyber Threat Intelligence: Uses up-to-date intelligence to detect emerging threats and new attack patterns before they can cause harm.
- Identifying Anomalies: Focuses on behavioral anomalies and deviations from normal network activity that could indicate compromise.
Methodology
High level continuous Threat Hunting process
Our methodology revolves around continuous, proactive threat searches conducted on various data sources such as networks, endpoints, and servers. We use tools like EDRs, XDRs, SIEM, and others to hunt for threats that cannot be detected through conventional methods. Our team works with your existing platforms, conducting tailored hunts based on hypotheses crafted specifically for your environment. These hunting campaigns are tracked through ongoing searches, queries, and analysis to uncover hidden risks. By partnering with you, we create a roadmap of recurring hunts, refining our approach as we go, and provide both detailed and executive-level reports on our findings. This approach ensures that your organization stays one step ahead of cyber threats.
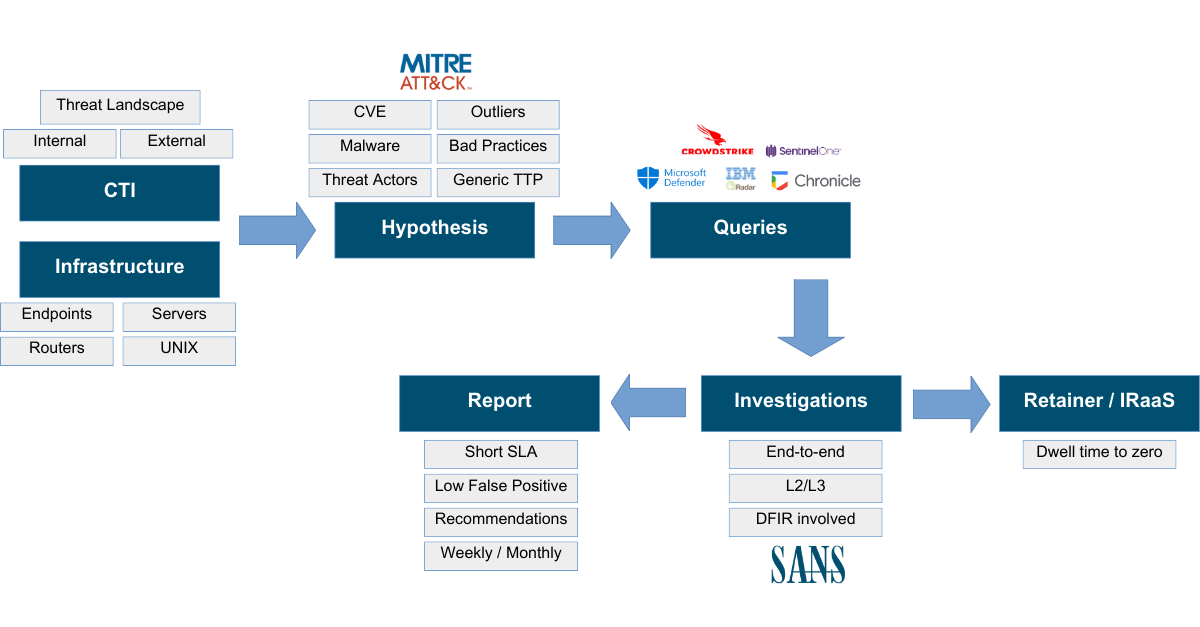
What Do We Hunt?
Threat Hunting is not limited to a single type of attack or threat; instead, it focuses on a wide range of potential risks within an organization’s environment.
Hunting Threat Actors and much more…
- Threat Actors: We hunt the most relevant cyber-criminal groups
- Generic TTP: The most commonly used by TAs, using sources such as Red Canary
- Bad Practices: We detect them to avoid potential incidents
- Malware: Malware most used by TAs such as Mispadu or Grandoreiro
- CVE: Based on our customers software
- Anomalies / Outliers: Look for deviations in the data based on AI, correlation, etc.
And not only with EDRs
Threat Hunting goes beyond endpoint detection and response (EDR). Our experts conduct investigations across multiple data sources, including:
- UNIX
- Routers
- SIEM / Other data sources
By adopting Managed Threat Hunting, organizations can significantly enhance their ability to detect, analyze, and mitigate threats before they escalate into major security incidents.
Client Stories
| Construction sector. Fortune 500 Europe | After an incident through their network devices attended by One eSecurity, we started a Threat Hunting service with EDR, SIEM, and some hunting types very uncommon and customer oriented, such as config. files in network devices and netflows, detecting different vector attacks before the intrusion was confirmed and wrong configurations in new network devices before they were exploited. |
| Food & Beverage sector. Bolsa Mexicana de Valores | Customer with an EDR and a SIEM that needs help to complement its team and get a more proactive perspective. We helped them by reviewing the tools alerts, investigating the most complex ones, and continuously introducing new queries in their platforms to cover their needs. They reduced the internal team needed and we helped stop some attacks with the queries we were introducing in the EDR. |
| Banking sector. Fortune Global 500 | Fortune 500 bank customer with multiple EDRs and tenants in many different countries. With our automation, we have been able to hunt in hundreds of thousands of assets and detect different attacks. |
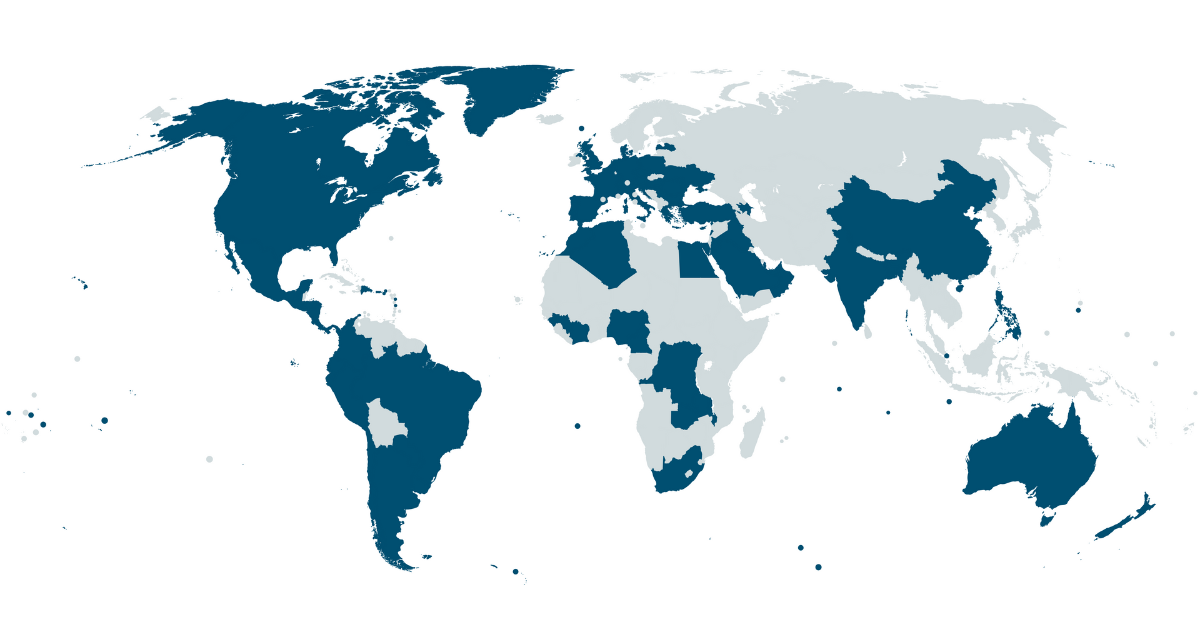
Global Threat Hunting Operations
Our Managed Threat Hunting services are actively deployed in over 60 countries worldwide, ensuring organizations across different industries benefit from a proactive approach to cybersecurity. The following map highlights where we are currently conducting proactive Threat Hunting operations.
Contact Us
Detect threats before they strike. Our proactive Threat Hunting service identifies malicious activities that other methods fail to detect. Protect your company before it’s too late.
📩 Request more information at sales@one-esecurity.com
⚠️ Experiencing a cyberattack? REPORT AN INCIDENT
Related To Our Services
| Digital Forensics and IR | Emergency Incident Response | Cyber Threat Intelligence |
|---|---|---|
| One eSecurity Digital Forensics service is focused on system in-depth analysis, aiming at obtaining a traceable record of previous activity in order to answer any investigative questions. | One eSecurity Emergency Incident Response is aimed at clients who need agile response and support when a security incident happens. | The Cyber Threat Intelligence service by One eSecurity provides (both internally and for clients) knowledge and information on key threats for decision-making and forecasts of risk situations on IT systems and networks. |
| Learn more | Learn more | Learn more |
