ONSITE • REMOTE • CLOUD
What Is SOC Empowerment?
Create new use cases for you SOC, the latest threats and the power of our Threats Hunting services, so your SOC can monitor them 24/7
SOC Empowerment is a strategic service designed to enhance the efficiency, capabilities, and overall maturity of an organization's Security Operations Center (SOC). By optimizing workflows, improving detection and response mechanisms, and integrating cutting-edge technologies, SOC Empowerment enables security teams to operate with greater effectiveness against evolving cyber threats.
Why Should You Use SOC Empowerment?
With the increasing complexity of cyber threats, traditional SOCs often struggle with alert fatigue, inefficient processes, and gaps in detection capabilities. SOC Empowerment addresses these challenges by:
- Enhancing Detection & Response – Improving the SOC’s ability to identify and mitigate advanced threats.
- Optimizing SOC Processes – Streamlining workflows to reduce incident response times and increase efficiency.
- Reducing Alert Fatigue – Implementing automation and advanced analytics to prioritize real threats.
- Integrating Threat Intelligence – Strengthening detection with up-to-date intelligence on emerging threats.
- Boosting Team Capabilities – Providing hands-on training and knowledge transfer to SOC analysts.
Methodology
Our SOC Empowerment approach follows a structured methodology to ensure measurable improvements:
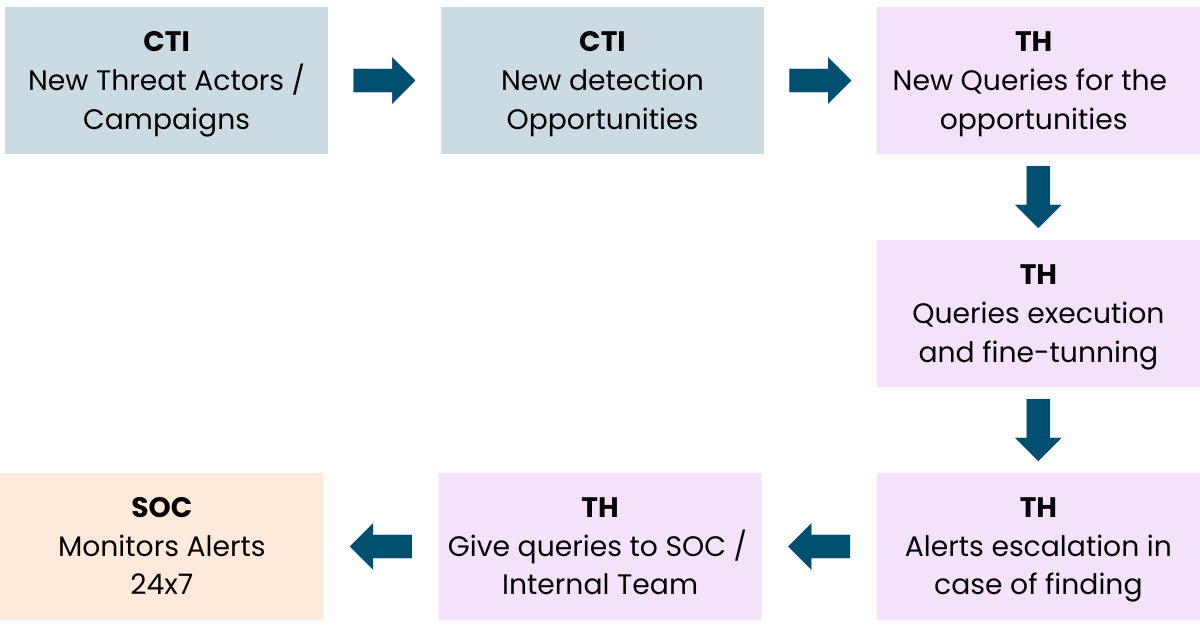
CTI (New Threat Actors & Campaigns)
We continuously monitor emerging cyber threat actors and their campaigns, providing the SOC with real-time intelligence on evolving attack methods and trends.
CTI (New Detection Opportunities)
By analyzing threat intelligence, we identify new detection opportunities, helping the SOC stay ahead of adversaries by creating and improving detection rules.
Threat Hunting (New Queries for the Opportunities)
Our experts develop new hunting queries based on identified threats and detection opportunities, ensuring proactive identification of malicious activity.
Threat Hunting (Queries Execution & Fine-Tuning)
We execute the developed queries, analyzing results and refining detection logic to minimize false positives while maximizing accuracy.
Threat Hunting (Alerts Escalation in Case of Findings)
If a threat is detected during hunting activities, our team escalates alerts with contextual intelligence, enabling a rapid and effective response.
Threat Hunting (Providing Queries to SOC/Internal Team)
Validated threat hunting queries are handed over to the SOC team for continuous monitoring and integration into existing security workflows.
SOC (Monitors Alerts 24×7)
With the improved queries and detection capabilities, the SOC monitors alerts around the clock, ensuring rapid detection and response to threats.
Contact Us
Empower your SOC and enhance your security operations with One eSecurity. Contact us today to learn how we can help optimize your SOC’s performance and resilience against cyber threats.
📩 Request more information at sales@one-esecurity.com
⚠️ Experiencing a cyberattack? REPORT AN INCIDENT
Related To Our Services
| Digital Forensics and IR | Emergency Incident Response | Cyber Threat Intelligence |
|---|---|---|
| One eSecurity Digital Forensics service is focused on system in-depth analysis, aiming at obtaining a traceable record of previous activity in order to answer any investigative questions. | One eSecurity Emergency Incident Response is aimed at clients who need agile response and support when a security incident happens. | The Cyber Threat Intelligence service by One eSecurity provides (both internally and for clients) knowledge and information on key threats for decision-making and forecasts of risk situations on IT systems and networks. |
| Learn more | Learn more | Learn more |
