ONSITE • REMOTE • CLOUD
What Is Threat Landscape Analysis (TLA)?
Ready to have a comprehensive view of your current threat landscape?
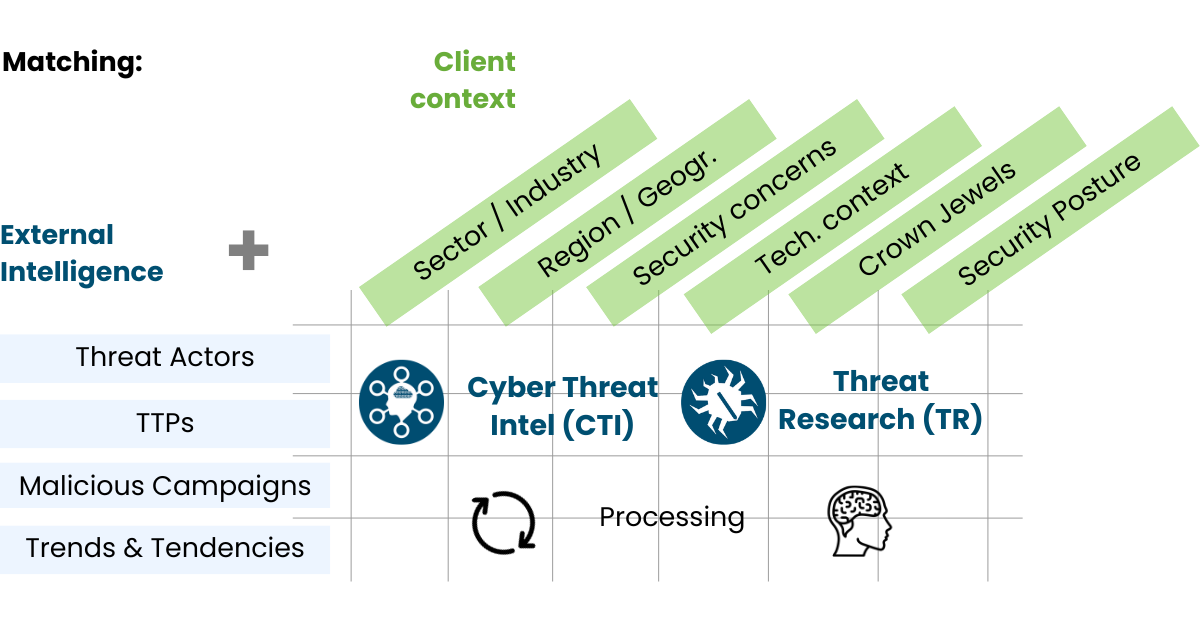
Threat Landscape analysis allow to search the threats that are most likely to affect your organization according your sector and presence, in order to identify and prioritize the most important TTPs based on the company's profile.
Why Should You Use TLA?
Key benefits of our threat landscape analysis project:
- Unparalleled visibility: Our team of experts leverages the most advanced tools and techniques to give you a 360-degree view of the threat landscape.
- Customized analysis: We understand that every organization is unique, so our analysis is tailored to your specific industry, size and risk profile.
- Prioritized information: We deliver a prioritized list of threats that can affect you the most, allowing you to focus your resources on the most critical areas of vulnerability.
- Strategic advantage: With the information at your fingertips, you can develop a proactive and tailored cybersecurity strategy, protecting your organization from emerging threats.
Methodology
This comprehensive, customized project will give you a thorough understanding of the specific threats facing your organization, enabling you to make informed decisions and implement effective cybersecurity measures.
Contact Us
Understand your threat environment. Identify emerging threats, vulnerabilities, and attack vectors specific to your industry and organization. Strengthen your security posture with expert insights.
📩 Talk to our specialists at sales@one-esecurity.com
⚠️ Experiencing a cyberattack? REPORT AN INCIDENT
Related One eSecurity Services
| Threat Hunting | Emergency Incident Response | Cyber Consulting |
|---|---|---|
| Our Threat Hunting service combines the analytic capacity of our most experienced experts with the power and automation of our Hunting Framework, offering a continuous and proactive threat search process in both networks and systems. | One eSecurity Emergency Incident Response is aimed at clients who need agile response and support when a security incident happens. | One eSecurity CYCON service can give you honest answers to the most complex questions and acting as a guide throughout decision-making processes. |
| Learn more | Learn more | Learn more |